Everyone knows coronavirus is on the rise, and there’s a lot of misinformation being provided to the public. Earlier this week on Twitter, there was a fake BBC website that claimed Harry Potter himself (Daniel Radcliffe) had gotten the coronavirus. Buzzfeed quickly debunked this. Still, the trend lasted for hours on social media.
If a fake Twitter account can cause such a fuss by disseminating false information, what could a real cybercriminal do to the public? Metro spoke to Sherrod DeGrippo, Senior Director, Threat Research and Detection at Proofpoint, all about how cybercriminals are capitalizing on the COVID-19 panic.
DeGrippo told Metro that for over five weeks, they have seen a lot of COVID-19 malicious email campaigns that capitalize on the fear surrounding the virus. They told Metro that criminals have sent email waves ranging from a dozen to 200,000. At first, Proofpoint reported that there was one campaign a day, but they reported that it’s grown to 3-4 malicious campaigns surrounding the virus a day.
DeGrippo told Metro that there are five common “lures” that cybercriminals use to trick people when it comes to COVID-19. They are outlined below:
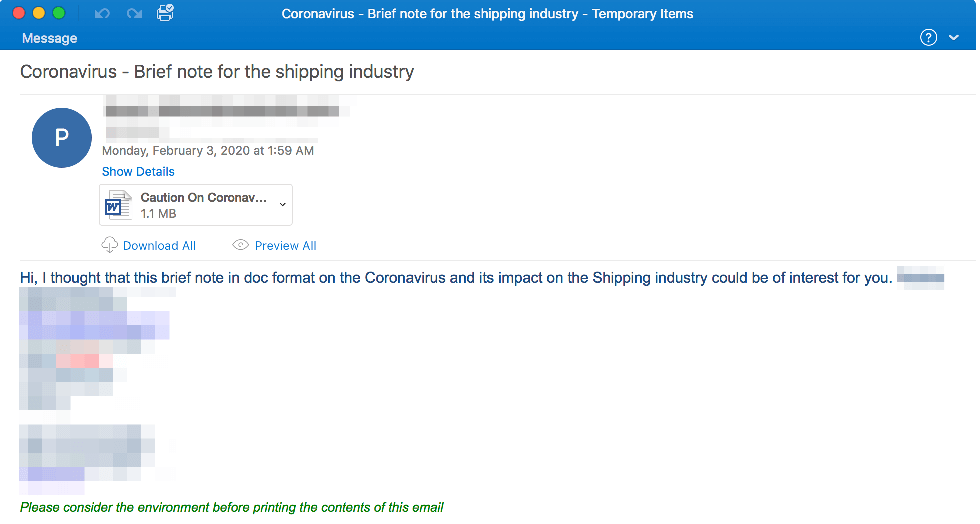
Global Shipping
- These messages are focused on the concerns about a virus’ impact on global shipping.
- It targets industries such as manufacturing, industrial, finance, transportation, pharmaceutical and cosmetic companies.
Claiming there is a cure hidden by the government

- These “lures” claim the cure is being hidden by the government because it is being used as a bioweapon.
- Recipients will likely be asked to click a link for more information.
- Once the link is clicked, recipients will be taken to sign a fake DocuSign website, where they need to enter a username or password to get the information.
Company Emails

- This type of email is supposed to look like an internal office email.
- It will likely claim to be emailed from a company.
World Health Organization
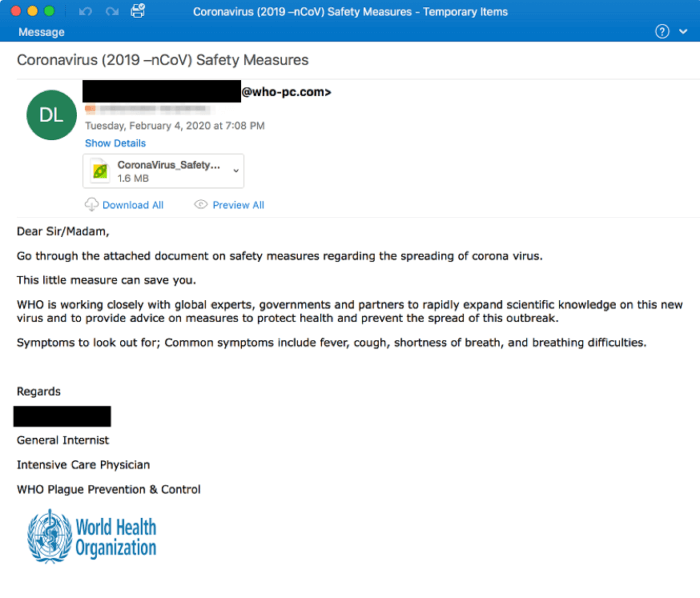
- Some criminals are pretending to be the World Health Organization.
- Those emails will likely claim to be a COVID-19 advisory.
Airlines
- Another common lure is criminals pretending to an airline.
As the COVID-19 themed emails infiltrate inboxes, here’s how to tell if a cybercriminal is targeting you. According to DeGrippo, “It’s extremely important to approach your inbox with the same level of caution you use in your non-digital, real life.”
When it comes to cybercriminals, they have gotten smarter over the years, and Metro was told that often attackers will use Google and LinkedIn to target victims. The emails that they send often look “very realistic, play on human psychology, and most require the victim to click a link or open an attachment to cause damage.”
DeGrippo added, “Take note if you receive an email that seems out of the ordinary or is asking you to take urgent action and trust, but verify, before clicking and acting if something seems off. For example, if your boss emails you asking that you urgently wire funds to a new bank account, be sure to confirm authorization verbally as it could be a fraudulent email.”
Another red flag when it comes to fraudulent emails is when they ask you to re-enter your username and password, ask for money, open or attachment or if they threaten to suspend service. Sometimes attackers can make it look like the emails come from a trusted source.
When it comes to safety, DeGrippo says that, “If you receive a suspicious email, you can hover your mouse across any presented link to make sure the address is what it purports to be, or better yet, type out the intended address in a browser window instead of clicking on the one in the questionable email. Confirm all transactions and requests via phone if you have concerns.”
DeGrippo continued, “Watch for spelling and grammatical errors; or attachments to documents or files that weren’t requested or expected. Finally, as an overall safeguard, use strong passwords, changing them frequently, and never reuse them across multiple accounts. If your provider offers multi-factor authentication, sign up for it and turn it on.”
If someone clicks a link to one of these cyberattacks, DeGrippo suggests implementing a “security freeze,” on all credit accounts and calling all credit-reporting agencies. It suggested that if you fear you’re a victim of a cyberattack, change your passwords.
As the COVID-19 panic grows, Proofpoint expects to see attackers focusing on targeting corporate workers in hopes of securing their financial information and credentials.
DeGrippo told Metro, “We’re now seeing a push in the United States for people to work from home or stay home from school. Threat actors may try sending malicious emails regarding remote access and fake corporate websites, all aimed at ensnaring teleworkers. “
DeGrippo added that if someone is concerned about their work email being targeted or that their work computer is compromised, contact the office’s IT staff immediately for help.